Multi-party disclosure - how does it work?
By our experts
In the past weeks, NCSC-NL has published several reports on a multi-party disclosure process. In this blog, I explain the difference between 'normal' coordinated vulnerability disclosure and multi-party disclosure processes. I describe what the different roles are in such a disclosure process and which role NCSC-NL can have. I end with some complications that may come up in such a process.
Coordinated Vulnerability Disclosure
Coordinated Vulnerability Disclosure (CVD) is the term for the `regular' process that precedes revealing vulnerabilities in a product or service that is in use at a single organization. This process can be summarized in a number of steps: It begins with someone who finds a vulnerability in a product or service. The finder then contacts the organization that uses this product or service to describe the vulnerability to them. The receiving organization starts to remediate the problem with a patch or some other mitigating measures. Finally, the finder and the receiving organization discuss how to publish the vulnerability. This process and all the preconditions are further described in the CVD guideline. In the past, this process was referred to as Responsible Disclosure.
The NCSC advises organizations to publish a CVD policy with contact information and the preconditions for reporting. This makes it clear for finders and researchers that the receiving organization is open to receiving reports about vulnerabilities. The published policy also gives some guidance for finders and researchers on acceptable behavior when looking for vulnerabilities.
In the 'regular' CVD process, NCSC-NL only has a role when it concerns a vulnerability in systems of NCSC-NL itself, or as a contact point for Central Government organizations (if they do not have a contact point themselves). Sometimes, NCSC-NL can act as a mediator when the finder and receiving organization cannot resolve the matter.
Multi-Party Coordinated Vulnerability Disclosure
With Multi-Party disclosure, there are multiple parties involved in the CVD process. Usually, there are multiple receiving organizations. This can be about a vulnerability in multiple products, or the same product that is in use at multiple organizations. In a multi-party disclosure process, this does not only concern coordinating the disclosure, but also coordinating with and between the different parties.
In a multi-party disclosure process, it is often necessary to have someone coordinate and guard the process. NCSC-NL can take on this coordinator role to help support the process when the vulnerability is relevant for our constituency, as described in the CVD guideline.
An example of a multi-party CVD process is a research project in 2015 where it was discovered that default passwords of wireless routers were predictable. Researchers of the Radboud University contacted NCSC-NL to support this process. NCSC-NL then used its network and informed the different internet providers in the Netherlands. The providers discussed with their suppliers to make updates available and make changes in the supply chain. With a handful of internet providers, each with different suppliers, soon a significant number of parties were involved. This made it necessary to have agreements that were clear for everyone, while at the same time maintaining confidentiality.
Difficulties of Multi-Party Disclosure
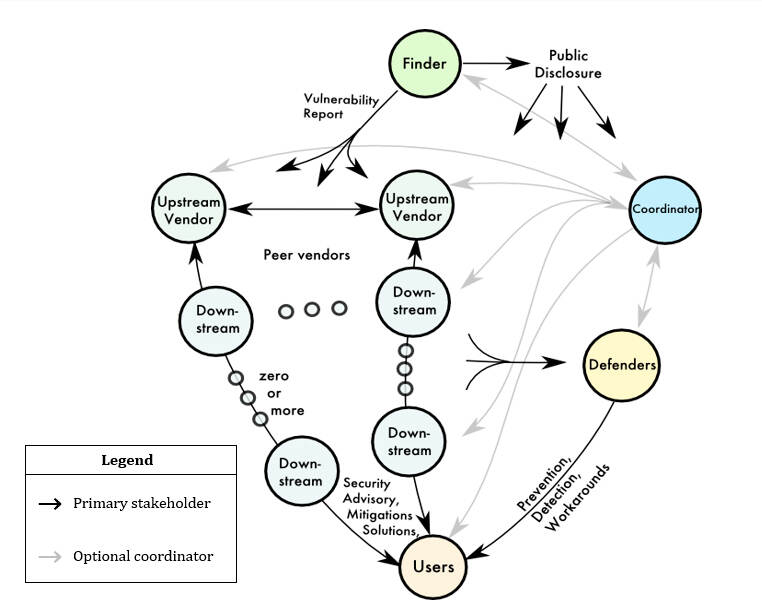
A multi-party disclosure can quickly become much more complicated than a regular vulnerability disclosure process. The international security community published a guideline in 2020 on multi-party disclosure with advice and points for consideration. The first diagram of this guideline shows the different roles and relations, making it clear that this can be a complicated process.
With different organizations, there are different interests and cultures. Factors that play a role in this process are, for example, the open-source communities, bug bounty programs, the increasing complexity of supply-chains or the different roles of security teams at vendors and other organizations. Each have a role and interest in revealing and mitigating vulnerabilities, and each in their own way.
The different interests also mean that these interests must be balanced and weighed. The interests of national security and the security of the Internet as a whole are important for NCSC-NL. For commercial parties, there is a commercial interest, and for many parties it is about the amount of work that has to be committed at some point. Additionally, CVD is a confidential process where not all information can be shared with everyone at any moment.
NCSC-NL has coordinated and participated in several of these multi-party disclosure processes in recent years. We keep in touch with relevant parties to discuss the best approach and evaluate our approach constantly. We use these evaluations to improve our own processes, and share these findings with others. We will also do this with the RPKI disclosure process.
Leave a comment
You can leave a comment here. Inappropriate comments will be removed. Comments are limited to 2,000 characters.
Comments
No comments have been published yet.