Expert Blog: Consumer routers targeted by multiple botnets
By our experts
The National Cyber Security Centre (NCSC-NL) has, following an incident response investigation, detected two botnet malware families simultaneously on a consumer router: Alogin botnet malware and TheMoon malware. This blog post explains the investigation and takes a closer look at the two malware families.
Incident response investigation
The malware families came to light during an incident response investigation into suspicious activity observed on ASUS network routers of businesses and consumers. These routers are used by both individuals and businesses for their internet connection. This explicitly concerns own equipment that consumers and businesses expose publicly to the internet and does not concern network equipment provided by internet service providers.
The suspicious internet traffic was discovered because the IP addresses of these routers were reported due to frequent authentication attempts on SSH servers. These login attempts were reason enough for the NCSC to, together with our partners, visit the owner of one of the compromised routers. The investigation was carried out on site. The NCSC was able to identify unknown malware samples deployed on vulnerable devices.
Forensic analysis
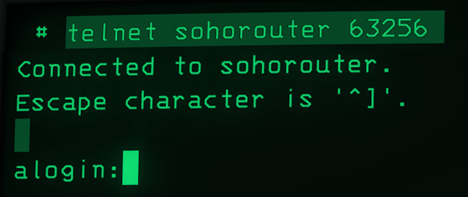
The incident response investigation into the Alogin botnet led to the owner of an ASUS RT-AC66u router that had an exposed telnet port with the alogin: loginprompt. The owner of this router voluntarily gave the NCSC access to the hardware for forensic investigation. The RT-AC66u router was running the latest firmware version, was directly connected to the internet and the default password had been changed by the owner on initial installation.
As is often the case with embedded Linux systems, the root file system of the affected ASUS router is 'read-only', with writable partitions usually mounted as writable ”ramfs”. We expected the malware to reside in these writable areas, so we began our investigation there. Given the potentially volatile nature of the malware, files had to be extracted while the router remained powered on, as any loss of power could lead to the loss of evidence.
To secure the malware, the NCSC-NL developed two methods: the first involved the use of a serial cable connected to the UART pins on the router's circuit board, and the second used a feature in ASUS routers that automatically runs a script from a USB stick when connected. Since the latter method was less invasive, we chose to use it-and with success.

Malware analysis
As a starting point in the search for malicious activity, the processes running on the infected router were listed and compared with those on an identical, uninfected router. The differences were immediately obvious. The directory listing of the /tmp directory also showed striking differences compared to the uninfected router.
A few things stood out: there were numerous processes with the same name, and two separate processes, /tmp/microso and .sox, both seemed to be running the open-source 'microsocks' proxy software. In addition, the timestamps of the files in the /tmp directory were strikingly different. The alogin and microso binaries had been created on the same day, several months before the .nttpd and .sox files.
This clearly pointed to two separate sets of malware samples. Further binary analysis of these files revealed enough similarities and differences to conclude that these were two completely different types of malware infections. It seemed that we had found two botnets operating simultaneously on this ASUS router.
Output of `ps` command
PID USER VSZ STAT COMMAND 10704 admin 1632 S telnetd -p 63256 -l /tmp/alogin 10965 admin 376 S /tmp/microso -u -P -p 63260 -d a 14836 admin 900 S ./.nttpd 14842 admin 828 S ./.nttpd 14844 admin 900 S ./.nttpd 14845 admin 900 S ./.nttpd 14846 admin 900 S ./.nttpd 14847 admin 900 S ./.nttpd 14848 admin 900 S ./.nttpd 22298 admin 2280 S ./.sox 22304 admin 1008 S ./.sox 22306 admin 2280 S ./.sox 22307 admin 2280 S ./.sox 22308 admin 2280 S ./.sox 22309 admin 2280 S ./.sox 22310 admin 2280 S ./.sox 22311 admin 2280 S ./.sox 22312 admin 2280 S ./.sox
Output of `find /tmp` command
/tmp/.tst /tmp/.sox.pid /tmp/.sox /tmp/.tst.out /tmp/.nttpd.pid /tmp/.nttpd /tmp/.nttpd-z /tmp/asi.sh /tmp/microso /tmp/alogin
Impact
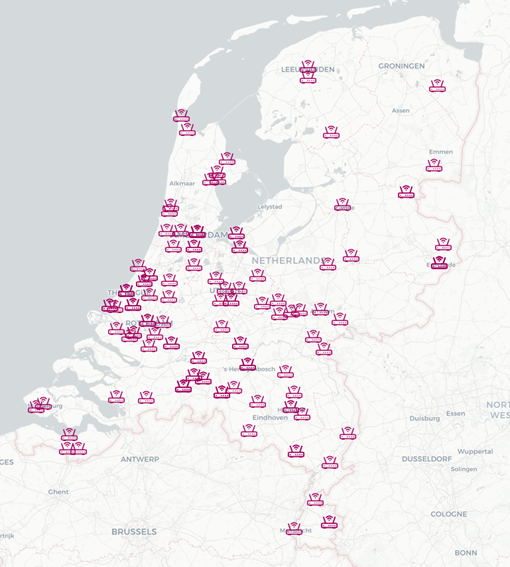
- The NCSC has recognised about 150 'small office and home office' routers (SoHo routers) in the Netherlands that are believed to have been compromised and recruited into such botnets. Globally, we estimate that these are part of a network of 13,000 compromised systems.
- Multiple sources have reported that systems within these botnets have been used for low-volume authentication attempts against some Microsoft cloud services.
- Abuse databases show numerous reports of brute-force SSH login attempts originating from victim IP addresses during the Alogin botnet infection period. While we cannot directly attribute these actions to malware, the consistent patterns in the abuse reports and the fact that our research focuses on typical consumer internet connections lead us to suspect, that in the vast majority of cases, these activities are probably not attributable to internet users.
- It is suspected that these botnets are offered as a 'service' to actors for malicious purposes.
How do I know if I am affected?
The NCSC-NL has released a script on GitHub for users of ASUS routers. This script can be placed on a USB stick and run to check for possible malicious processes and files.
Please note that this script may not work on all ASUS router models and may not detect all types of malwares. It is merely an indication of infections related to the findings discussed in this blog.
Mitigation measures
However, the following mitigation strategies are always more effective in the long run and should be prioritised, as the USB script is not a watertight solution and should be considered as a last resort.
- Check regularly for vendor firmware updates and ensure that network devices are kept up to date.
- Keep all network devices updated and replace devices that are no longer supported by the manufacturer.
- Avoid exposing network devices directly to the internet without implementing proper security measures (for consumers, and for SMEs and larger).
- If you are not sure how to secure your own Customer Premise Equipment (CPE), consider using the equipment provided by your Internet Service Provider (ISP).
In addition, the NCSC-NL is actively working with partners to contact and send notifications to affected parties.
Two types of malware families
Related findings
- The router also contained traces of a third malware infection, likely related to this sample:
3434839b2392f6fc729f428ac1eeb989b6c79e366e95b5236d8deaafd7489bf4 - Another possible botnet has been discovered targeting the same group of devices and running an SSH server on port 63257 with an "SSH-2.0-GO" banner. The number of affected devices meeting these criteria is currently estimated to be around 930.
Responsible disclosure
NCSC has reached out to ASUS and shared these findings with the vendor. As a response ASUS has released patched firmware versions for affected devices that are still supported by the vendor, as well as a number of devices that have been out of support.
Users of ASUS routers are advised to update their router firmware as soon as possible and read the recently published ASUS security advisory.
For devices that no longer receive any patches, ASUS recommends users to take the following measures:
- Reset the router to factory settings
- Disable all remote access services such as WAN access, AiDisk, AiCloud, FTP, VPN and port forwarding
Special thanks to
- gi7w0rm for sharing information from the eye of the storm
- Sekoia for their detailed report and demonstrated expertise in analysing hardware infected by the quad7 botnet.
- Team Cymru for publicly sharing their findings on the alogin botnet.
- Our partners and stakeholders who helped us along the way.
- Above all: The family who welcomed our team into their home and allowed us to conduct a forensic analysis in their living room.
Join us
Want to get paid to do research like this? The NCSC-NL is looking for new colleagues! Check out our open vacancies on werkenvoornederland.nl.
Indicators of Compromise
The Indicators of Compromise (IoCs) are attached to this post.
More blog posts
Leave a comment
You can leave a comment here. Inappropriate comments will be removed. Comments are limited to 2,000 characters.
Comments
No comments have been published yet.